Security Information
Brilliance CRM offers a security architecture that meets and exceeds industry standards and is designed to protect sensitive data and ensure the privacy of your business. We utilize AES-256 encryption, the industry standard for data security, to secure fields and databases, safeguarding them against unauthorized access. For password protection, Brilliance CRM employs Argon2, an award-winning, highly secure hashing algorithm, ensuring that user credentials are securely encrypted and resistant to brute-force attacks. Additionally, the system integrates Ed25519 for digital signatures, providing a fast and secure method for verifying the authenticity and integrity of documents.
To further enhance security, Brilliance CRM is equipped with both local and global firewalls that monitor and control incoming and outgoing network traffic, protecting against potential cyber threats. Two-factor authentication adds an extra layer of security, requiring a password and a second factor to verify user identity. Moreover, users have the ability to customize page headers, adding another layer of protection to protect web pages from common vulnerabilities and attacks. These comprehensive security measures make Brilliance CRM a secure choice for managing sensitive business data.
Key Features For Security
Brilliance CRM sets the industry standard with unmatched protection and seamless ease of use. Every user benefits from a powerful, built-in security suite designed to detect, prevent, and respond to threats in real-time—ensuring your business and customer data remain protected at all times.
Unlike other CRM platforms that require complex configurations, Brilliance CRM's advanced intrusion detection system works automatically — no setup, no hassle, just enterprise-grade security from day one. We take a proactive, AI-driven approach to threat detection, blocking malicious activity before it becomes a problem.
Whether you're a business or government agency, Brilliance CRM delivers unparalleled security, combining firewall protection, AI-driven threat mitigation, and real time monitoring—making us the most secure CRM solution available.
Database Information
- AES-256 encryption
- Daily Backups
- Dedicated Database
- HIPAA Compliant
- On-site or Cloud
Email Sequence Notifications
- Blocked Country, IP Address
- Change Password
- Dark Web notifications
- Email and/or Text Notification
- Login
- Logout
- Notification of Failed Logins
Forms and Email Protection
- Bad Word Lists
- HIPAA Protection
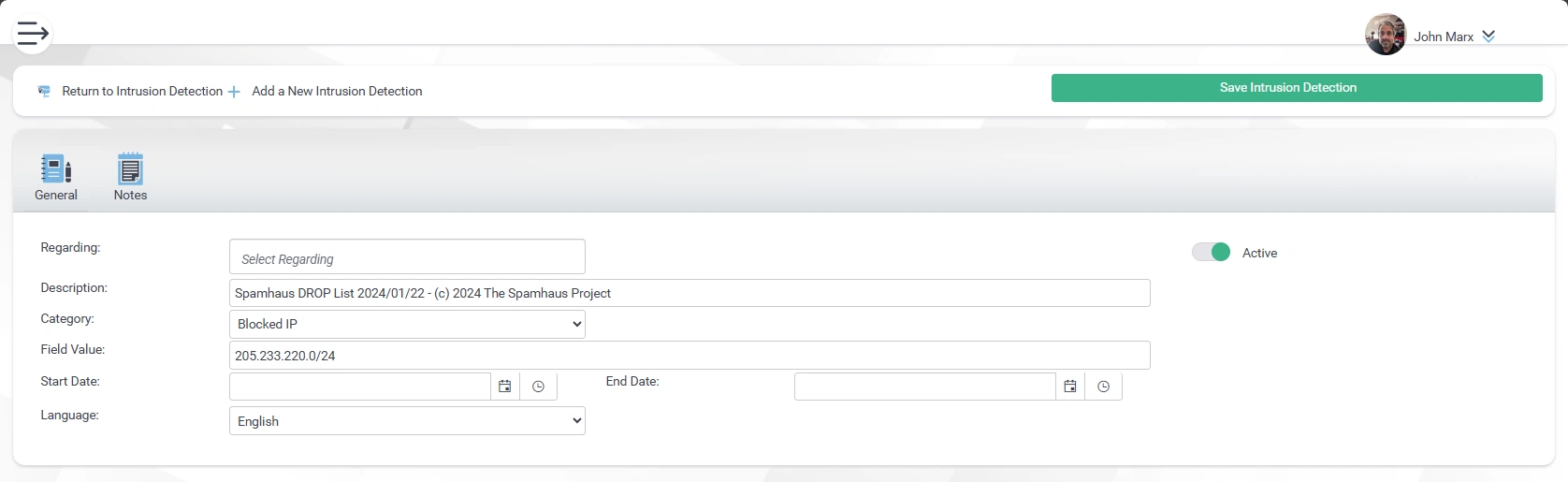
Intrusion Detection
- Block Countries
- Block Bad Passwords
- Honey Pot
- IP Address Blocks
- Automatic
- Manual
- Temporary
Malware & Anti-virus Protection
- Check: All Modules
- Check: All Documents
- Malware Monitoring and Checking
- Virus Monitoring and Checking
Network Infrastructure
- 24x7x365 Monitoring
- Hardware
- Servers
- Site
- Firewall
- Hardware
- Software
- Full HIPAA Compliance
- Microsoft Azure Network
- Penetration Testing
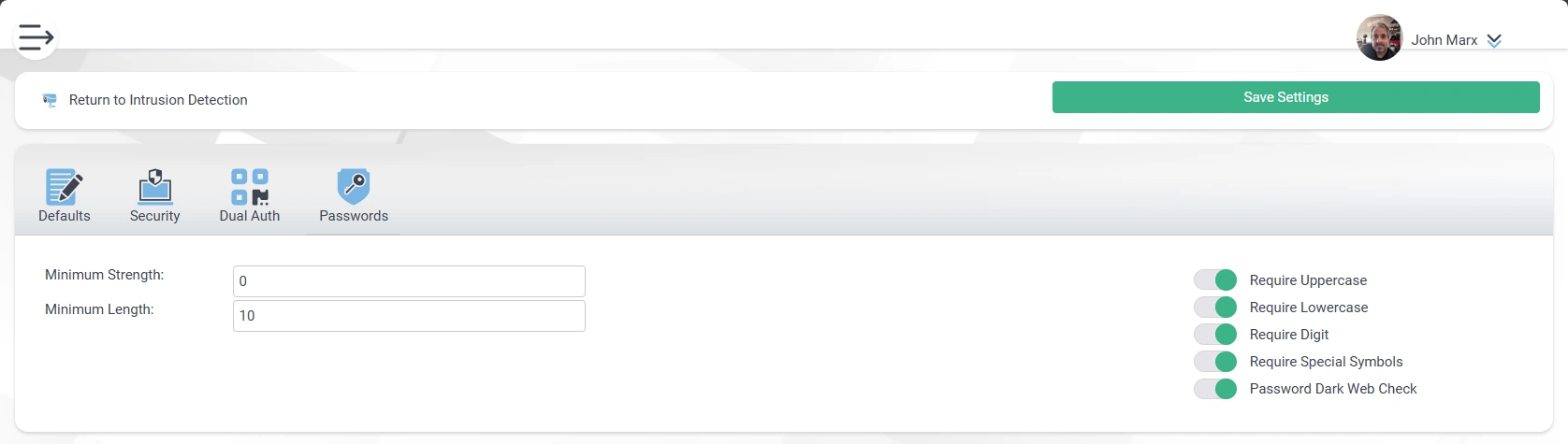
Password Control
- Argon2 Encryption
- Minimum Length
- Minimum Strength
- Password Options
- Force UPPERCASE
- Force lowercase
- Force Digits
- Force Symbols
Role-Based Access Control (RBAC)
- Easily see who is in each group
- Fields are hidden based on user role
- Multiple Groups per user
- Unlimited Groups
System Login
- Automatic Lock Timeout Periods
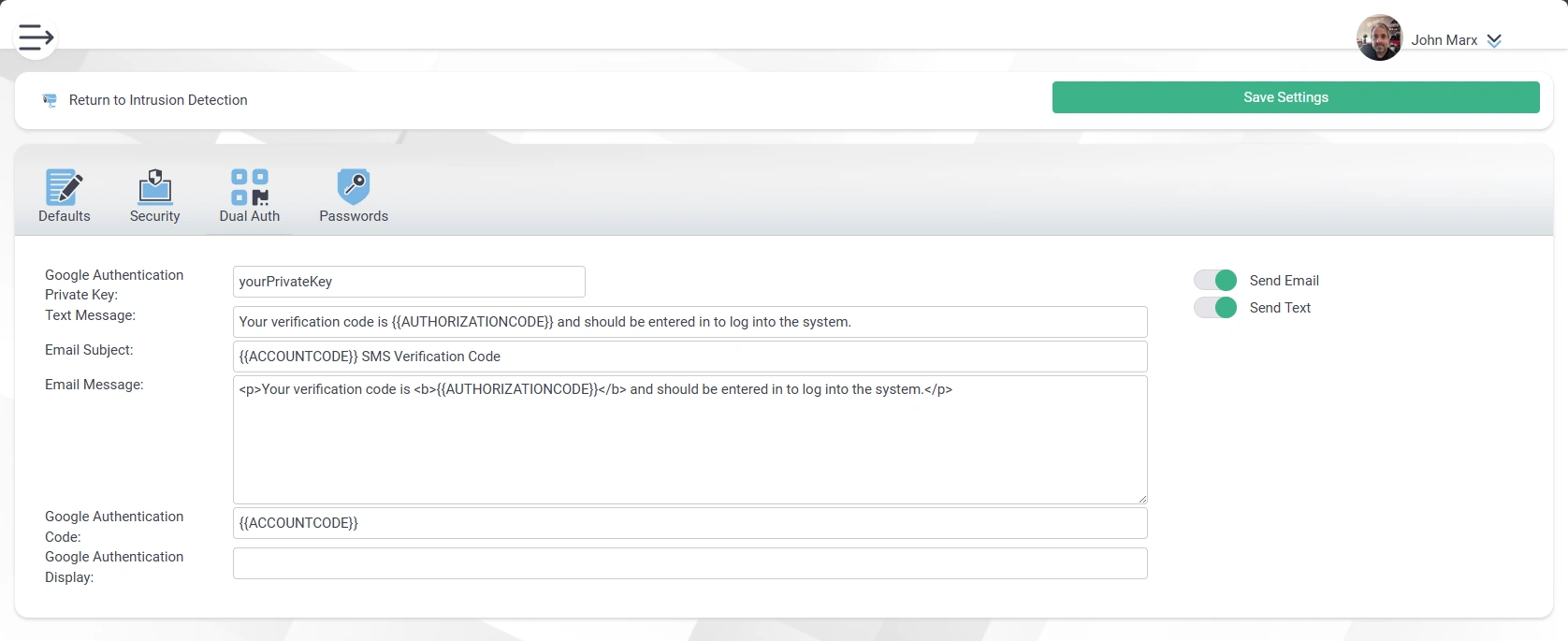
- Two Factor Authorization (TFA)
- Google Authenticator
- Microsoft Authenticator
- Text / SMS
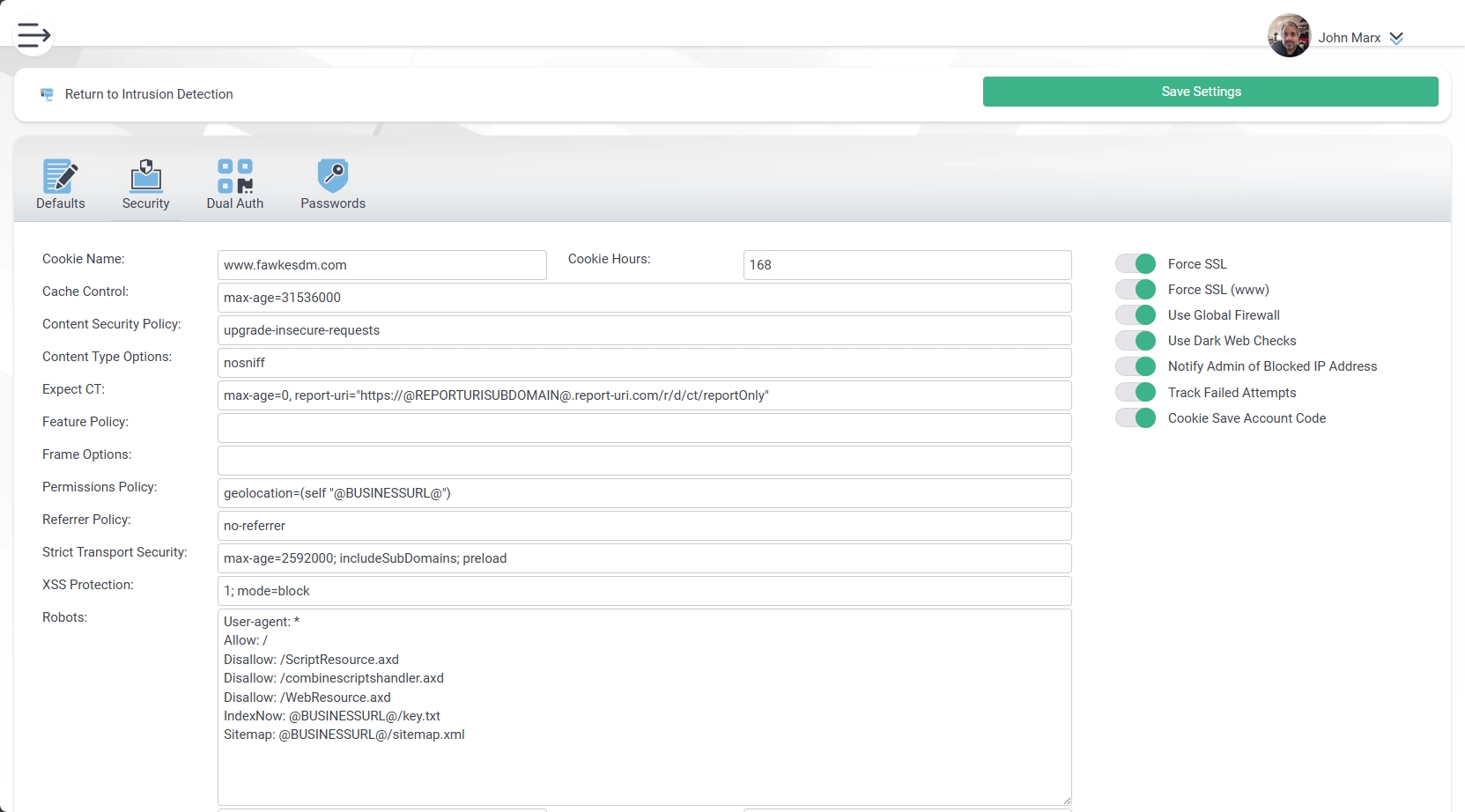
System-Wide Page Headers
- Cache-Control
- Content Security Policy
- Content Type Options
- Expect CT
- Feature Policy
- Frame Options
- Referrer Policy
- Strict Transport Policy
System Wide Security
- AES-256 Encrypted Fields
- Cookie Control
- Ed25519 Digital Signatures
- Force SSL (TLS) on all pages
- HIPAA Level Enhanced Logging
- Robots.txt file
- Security.txt file
- Zero trust for all modules